Android penetration testing is a complex process that can be scary for those who are not familiar with it or have a technical background. The purpose of this blog post is to break down the basics and provide you with all of the information you need to know to start an Android penetration test of your own.
What is Android Penetration Testing
Android penetration testing is not necessarily Android-specific, but it uses the Android OS as its platform. It is a crucial part of the app development process. It involves various techniques that are used to identify vulnerabilities in Android apps and then exploit them for malicious purposes. Android penetration testing is an essential step of Android app security. All Android developers who want to ensure that their apps are as secure as possible conduct pentests. Android penetration testing can help find vulnerabilities that automated tests miss, including security scans and black-box tests.
Types of Android Penetration Testing
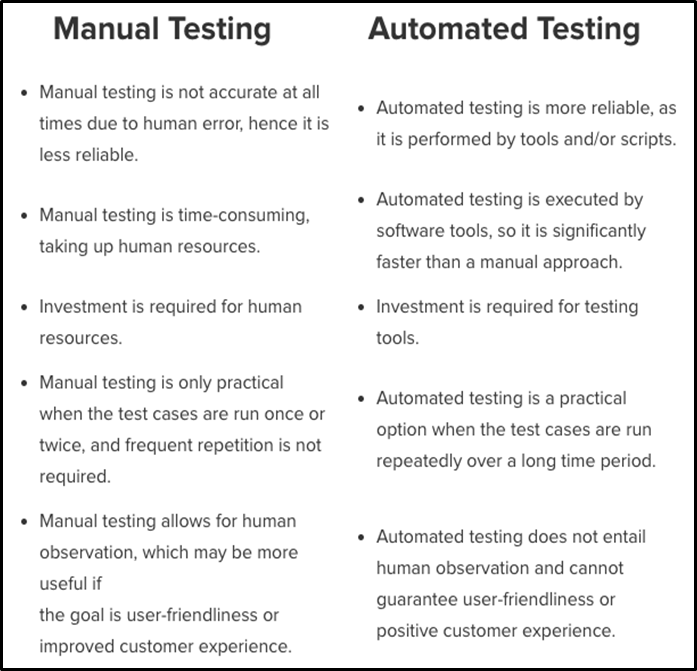
Manual Android Penetration Testing
This type of penetration testing requires the android developer to manually try attacking his own android application with various hacking tools, techniques, or even by themselves. This process takes a lot of time because you have to manually identify vulnerabilities. It may take days before reaching 100% completion. On top of being very slow, they are not efficient for developers who have hundreds or thousands of apps they want to test on.
Automated Android Penetration Testing
Automated android penetration tests are conducted using software or apps that perform android penetration tests from a remote location, without requiring any prior knowledge of the android app and its features. Many android developers prefer this type because it’s very easy to use. It can also be completed in just one day depending on how complex your application is.
Various Stages of Android Penetration Testing
Stage One: Reconnaissance
The first step of an Android penetration test is Reconnaissance. This basically means mapping out your target environment in order to determine what devices are present and where they’re located on the network. Testers do this by scanning IPs with tools like nmap or zmap/zgrab in order to discover services running on various ports that could lead you into a vulnerable state if attacked.
Stage Two: Threat Modeling & Vulnerability Identification
It is based on research conducted after reconnaissance, threat modeling involves identifying potential vulnerabilities within each identified service discovered during recon while vulnerability identification specifically pertains to exploitation methods used against said vulnerabilities once found. You’d typically want to start with the most obvious services and/or vulnerabilities first so as to expedite this process.
Stage Three: Exploitation
Android penetration testing is not necessarily Android-specific, but it uses the Android OS as its platform. Android was originally designed for use on smartphones. Therefore, a majority of bugs found in Android are usually related to memory corruption due to bad input validation or data type conversion issues within certain functions that accept user-provided input without proper sanitization.
These types of vulnerabilities can often manifest themselves into what’s known as a buffer overflow – which basically means that if an attacker were able to exploit these errors they could run arbitrary code (i.e., malware) on you by sending specially crafted messages over TCP/UDP to Android services.
Stage Four: Post-Exploitation
Android penetration testing is not necessarily Android-specific, but it uses the Android OS as its platform. After you’ve exploited a service and gained access to Android devices on your target network there are still some things you can do such as deleting logs or manipulating device behavior.
You could also use this type of access in order to pivot into other parts of the network with additional attack vectors that were inaccessible from the outside due to lack of permissions (for example, if an app requires root privileges then these would be accessible once exploitation has occurred).
Stage Five: Resolution & Re-Testing
Now, you have to resolve all vulnerabilities that were identified during the test. You also have to work on remediation and enhancing overall security. Then, it’s time for another round of Reconnaissance, Threat Modeling, and Vulnerability Identification followed by Exploitation.
What To Look For In An Android Penetration Tester?
When hiring Android penetration testers, we recommend that you consider the following:
- Experience with mobile devices and operating systems.
- Ability to write scripts in bash/python/ruby/golang etc.
- Knowledge of Android security internals and Android-specific vulnerabilities.
- Good understanding of Android application architecture, Android APIs, and the Android build system.
Final Thoughts
If you want to ensure your app is secure and free from vulnerabilities, it’s a good idea to conduct an android penetration test. That means identifying the potential risks in your Android application by running various tests on it. After reading this blog post, you should have a better understanding of the basics of Android penetration testing.


![FPse for Android devices Apk v11.204 [Latest] FPse for Android devices Apk v11.204 [Latest]](https://www.androidappbd.com/wp-content/uploads/2018/03/FPse-for-Android-devices-Apk.png)
![CCleaner Pro For Android v5.1.1 Apk Premium [Latest+Mod] CCleaner Pro For Android v5.1.1 Apk Premium [Latest+Mod]](https://www.androidappbd.com/wp-content/uploads/2018/03/ccleaner-pro-for-android5.png)



![Package Disabler Pro Apk v15.0 All Android [Latest] Package Disabler Pro Apk v15.0 All Android [Latest]](https://www.androidappbd.com/wp-content/uploads/2018/03/package-disabler-pro-apk.png)